Browser Extensions¶
macOS Password AutoFill¶
On the Mac, you can easily access your safe from within your browser.
pwSafe 11.0, to be released in February 2025, will provide support for native macOS Password AutoFill. More information on this exciting new feature is available on our support site.
Unsupported Safari versions¶
Safari 11 or 12¶
To install the extension on Safari 11 or 12:
- Download the extension by clicking on the Safari icon above and then follow the authentication procedure below.
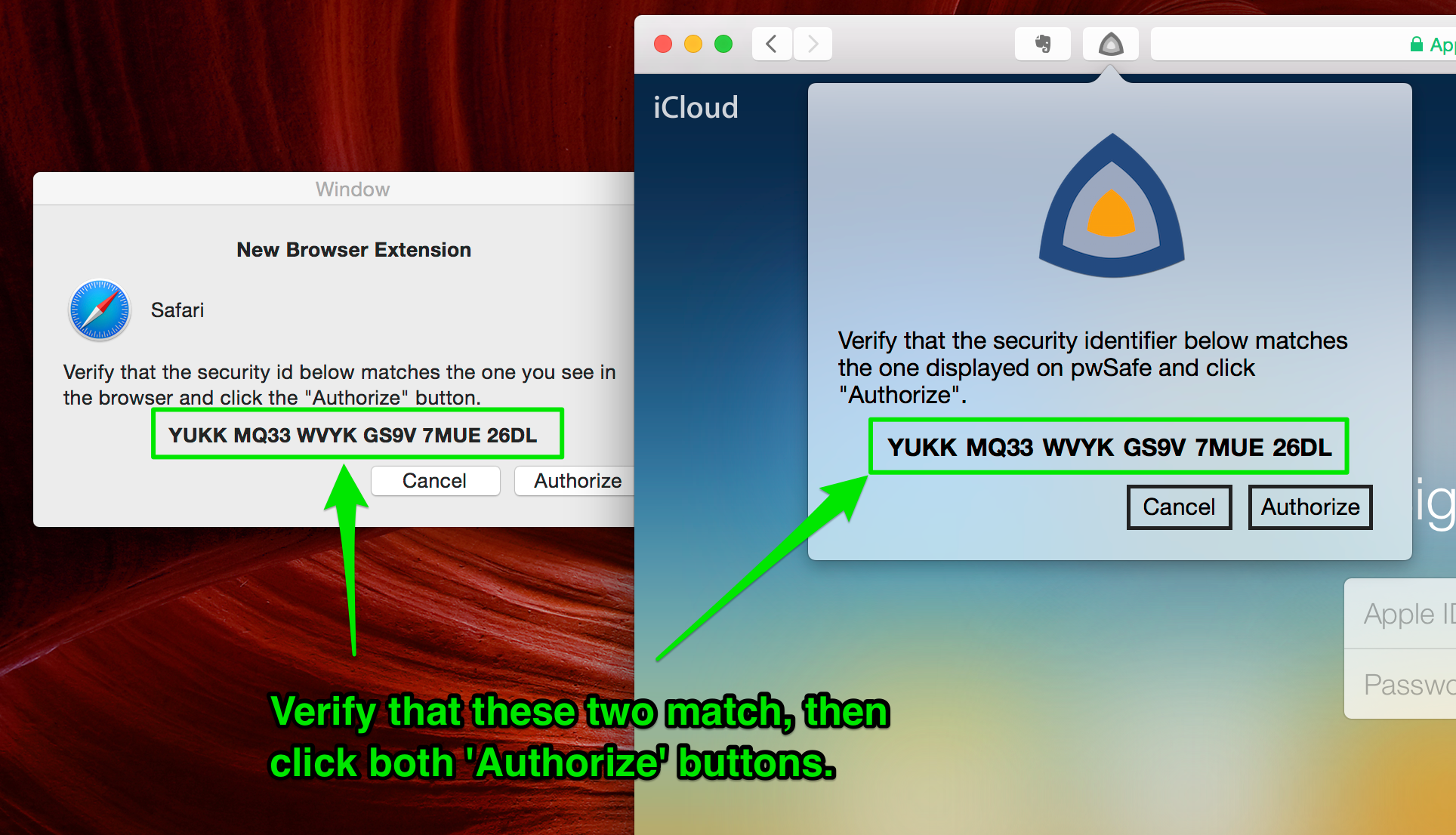
Authentication¶
After installing your browser extension, you'll be asked to authenticate the communication between it and the pwSafe app. It's a simple process, just verify that the authentication code displayed by the extension inside your browser and by pwSafe match one another and click “Authorize” on both the app and the extension.
Understand why this is necessary on the security section below.
Usage¶
To use the extension, navigate to a page which has passwords fields and click the pwSafe icon on the browser's toolbar. You can also hit CMD + Option + P, unless the website is actively disabling hotkeys.
Tip
Experiment with the arrow keys and return key to use the extension without touching the mouse most of the time.
If your safe is not already unlocked, you'll have to choose it, and then enter its password so that pwSafe can unlock it. You can do all that using just the keyboard: use the arrow keys to move up or down and the enter key to select your safe from the list. After you've input your password, press the return key to unlock your safe.
Security¶
Modern browser extensions are javascript apps that run inside the web-browser. This makes them more susceptible to malicious websites and also very restricted when it comes to interacting with the local machine. These two facts pose a series of security concerns that we address.
To defend against malicious websites:
- The full list of passwords is never sent to the extension, which only gets the password needed to fill the currently displayed webpage. When listing entries, it only gets titles, details (username and url) and groups.
- Extensions are broken in two main components: one running inside the displayed webpages (more vulnerable) and another one running in an isolated context (more secure). The component which runs on the webpage context can't connect to pwSafe directly, so it can't send commands to it asking for more passwords. It can only report which fields are present on the webpage and, when ordered to, fill them with the provided values.
To defend against malicious apps on your Mac:
- Communications between the extensions and pwSafe are run over a standard HTTP Websocket connection to localhost. Since the SSL certificate validation logic cannot be overridden by the extension, we use a non-encrypted HTTP connection with our own security (encryption and authentication) layer on top.
- Everything but the handshake is fully encrypted (AES-CBC-256) and authenticated (HMAC-SHA-256).
- When you first connect, both sides calculate an identifier which is a hash of both parties' public keys (RSA-2048) and display it to the user. The user then matches both, defending against man in the middle attacks.
- After validation, the extension and pwSafe save the other party's public key and verify it on every new connection, closing it if it changed, preventing man-in-the-middle attacks.
- On every session, new encryption and authentication keys are generated, so as to guarantee perfect forward secrecy (PFS).
- Session keys depend on both sides random number generators, making it harder to exploit a PRNG fault.
- Every data packet has:
- a new sequence number to prevent agains replay attacks, and
- a random initialization vector (IV).
When designing the extensions, we took great care to protect your passwords at all times.
If we failed to address any concern, please let us know.
